Mogicがつくるサービス
少子高齢化が進む日本、先進国。急速に人口が増える途上国。
生産性を高めるため、IT教育サービスでサポート。
ちいさなテクノロジー

日々の調査・研究成果を「MicroTech(マイクロテック)」として1ページにまとめました。
大きなプロダクトの一部になったり、サービスづくりのトレーニングになったり。掲載されるものはごく一部で、数週間ほどで1つのプロダクトが創られています。
よくある質問
サービスの立ち上げには、マーケッター/デザイナー/エンジニアという職種で企画を考えたのち開発やテストを行っています。また運営段階に入ると、カスタマーサポートが加わってクライアント対応や改善をとりまとめています。
IT分野は新しい技術が次々と登場してきます。ただし、ウェブサービスの運用に組み込むかどうかは慎重さが必要だと考えています。実験的なプロダクトであれば新しい技術をすぐに試しますが、大規模に運用されているサービスの場合は影響範囲が大きいため、テストを重ねてこなれた状態で組み込んでいます。
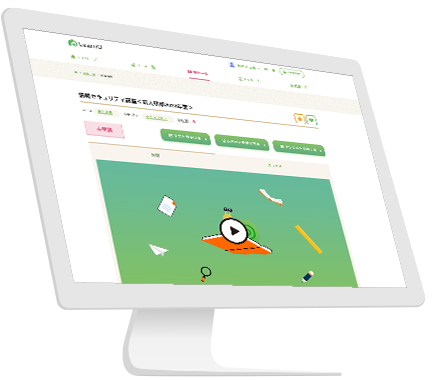
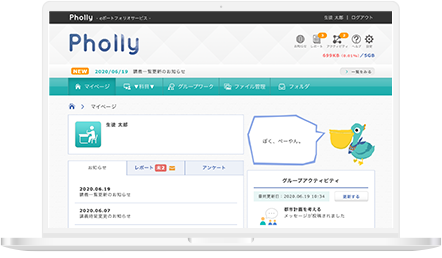
eラーニングシステムLearnOや授業支援システムPhollyという汎用サービスでは要望を満たせない場合にカスタマイズ開発プランをおすすめしています。ご要望に応じつつ、これまでの教育IT開発のノウハウでご提案させていただきます。
※eラーニング開発プラン:https://learno.jp/ordermade/
※eポートフォリオ開発プラン:https://pholly.jp/ordermade/
※Mogicらしいシステム開発とは:https://solino.mogic.jp/a/13825
大原則として障害が起きにくい仕様や設計開発を目指しています。それにより障害の発生頻度と影響範囲を最小化できるためです。急ピッチなリリースや余裕のないスケジュールでは不具合がでやすくなりますので最大限避けています。万が一サービスの障害が起きた場合、検知システムによりアラートが上がり、緊急連絡体制でなるべく早い復旧を目指して対応します。また第三者による悪意ある攻撃が増えていますので、常時サーバ並びに防御壁を監視して対処しています。
利用者数が多いサービスほどバージョンアップや改善の頻度が高くなります。小さなものを含めると年間50から100回ほど行われています。利用者が気がつきやすい改善もあれば、ページ表示速度を上げるためのプログラム改修まで多岐に渡ります。バージョンアップの回数が多いのは、すべて自社内で企画開発を行なっているためです。
もしご利用中のサービスで不具合を発見された場合はすぐにご連絡ください。不具合の報告が届くと社内のプロジェクトメンバ全員に素早く周知されて、確認作業が始まります。たまに不具合ではなく、仕様の場合がありますが、使い勝手の改善案として実装の検討をさせていただきます。
はじめてIT教育システムを導入される方は大勢いらっしゃいます。まずは何をしたい、これはできそうかと気軽にお聞きください。弊社のサービスでそれが実現可能なのかどうかを返答します。
お客さまよりお申し込みいただいた情報は、すべて自社独自の管理システムに取り込まれます。そこでアカウント権限ごとに接触できる担当を絞り、必要最低限の情報だけで次の業務につながるようにしています。また契約終了時など情報が必要なくなった場合に素早く削除し、保持しないように努めています。業務フロー全体のセキュリティは、ISMS監査及びプライバシーマーク審査の時に再度確認しています。